Making the internal network of company or corporation secure, requires a large amount of time spend and a lot of resources and effort. But there is always a weak point, a soft spot if you want, and that is the network centre. This soft spot is an attractive target for internal thieves or hackers. The Wikileaks’ “Cablegate” incident is one of most notorious examples, in which confidential and sensitive diplomatic cables from United States embassies worldwide, over 250,000 cables to be more exact, are thought to be stolen by a clerk in the US Department of Defence.
Internet data theft
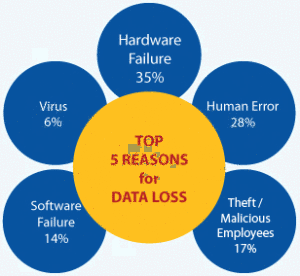 We could say that security is more of a state of mind. Protecting a company from internet data theft involves more the firewalls, gateway security or other complicated hardware or software solutions. Internal and also internet data theft risks should make every business start procedures to reassess in what and where the danger of exposing sensitive information is, to reassess the potential threats that they are facing and will have to face.
We could say that security is more of a state of mind. Protecting a company from internet data theft involves more the firewalls, gateway security or other complicated hardware or software solutions. Internal and also internet data theft risks should make every business start procedures to reassess in what and where the danger of exposing sensitive information is, to reassess the potential threats that they are facing and will have to face.
The threats can come from the company staff, but also from contractors with network access and other opportunistic external thieves. They are even more common as the modern storage devices can hold huge amount of digital data and the downloading speed gets faster and faster. Imagine how long it will take someone to connect a USB flash drive or an USB internet mobile connection device to a workstation and copy or download your entire customer database, payroll data, e-mail archive or your company’s financial reports, projections, opportunity or risk analysis or even market estimates. Also, this can be done with a regular smartphone, a USB wristband, a USB pen drive and even an iPOD. The methods are countless.
The fact is that you cannot control effectively the usage of mobile storage devices or other mobile devices that connect to external networks, because, in some instances, your personnel is required to access the USB ports to transfer and carry data files. One solution is to implement different staff and external parties’ restriction policies when they access your digital data. Also, mobile storage devices should be forbidden or highly restricted. But still, there will always be exploitable security holes for your employees or you will be exposed to internet data theft, as there is no such thing as a perfect secured network.

Data access
The best thing you can do is to restrict data access to only those that actually have to see it or modify that information. Your sensitive digital data should be classified and managed in a way that however or wherever you store it, if you get hacked, only a little piece of information will be revealed. Internal and internet data theft cannot be prevented if all your data is classified as sensitive, as this will enable everyone that will work with it to have access to the entire database or network. One commentator in the Wikileaks’ “Cablegate” affair stated that sharing secret information with 3 million users means that it was never a secret to begin with.
